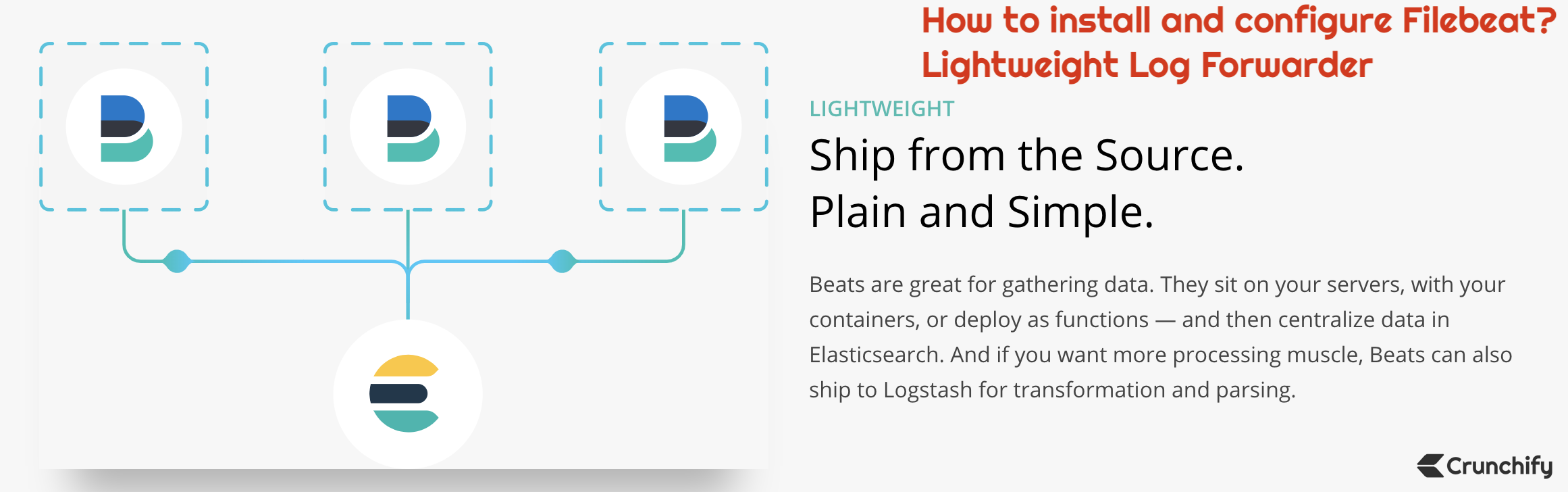
Over last few years, I’ve been playing with Filebeat – it’s one of the best lightweight log/data forwarder for your production application.
Consider a scenario in which you have to transfer logs from one client location to central location for analysis. Splunk is one of the alternative to forward logs but it’s too costly. In my opinion it’s way too costly.
That’s where Filebeat comes into picture. It’s super light weight, simple, easy to setup, uses less memory and too efficient. Filebeat is a product of Elastic.co.
It’s Robust and Doesn’t Miss a Beat. It guarantees delivery of logs.
It’s ready of all types of containers:
- Kubernetes
- Docker
With simple one liner command, Filebeat handles collection, parsing and visualization of logs from any of below environments:
- Apache
- NGINX
- System
- MySQL
- Apache2
- Auditd
- Elasticsearch
- haproxy
- Icinga
- IIS
- Iptables
- Kafka
- Kibana
- Logstash
- MongoDB
- Osquery
- PostgreSQL
- Redis
- Suricata
- Traefik
- And more…
Filebeat comes with internal modules (auditd, Apache, NGINX, System, MySQL, and more) that simplify the collection, parsing, and visualization of common log formats down to a single command.
How to Install Filebeat on Linux environment?
If you have any of below questions then you are at right place:
- Getting Started With Filebeat
- A Filebeat Tutorial: Getting Started
- Install, Configure, and Use FileBeat – Elasticsearch
- Filebeat setup and configuration example
- How To Install Elasticsearch, Logstash?
- How to Install Elastic Stack on Ubuntu?
Step-1) Installation
Download and extract Filebeat binary using below command.
Linux environment:
root@localhost:~# curl -L -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-6.7.0-linux-x86_64.tar.gz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 11.1M 100 11.1M 0 0 13.2M 0 --:--:-- --:--:-- --:--:-- 13.2M
root@localhost:~# tar xzvf filebeat-6.7.0-linux-x86_64.tar.gz
root@localhost:~# cd filebeat-6.7.0-linux-x86_64/ root@localhost:~/filebeat-6.7.0-linux-x86_64# pwd /root/filebeat-6.7.0-linux-x86_64 root@localhost:~/filebeat-6.7.0-linux-x86_64# ls -ltra total 36720 -rw-r--r-- 1 root root 13675 Mar 21 14:30 LICENSE.txt -rw-r--r-- 1 root root 163444 Mar 21 14:30 NOTICE.txt drwxr-xr-x 4 root root 4096 Mar 21 14:31 kibana drwxr-xr-x 2 root root 4096 Mar 21 14:33 modules.d drwxr-xr-x 21 root root 4096 Mar 21 14:33 module -rw-r--r-- 1 root root 146747 Mar 21 14:33 fields.yml -rw------- 1 root root 7714 Mar 21 14:33 filebeat.yml -rw-r--r-- 1 root root 69996 Mar 21 14:33 filebeat.reference.yml -rwxr-xr-x 1 root root 37161549 Mar 21 14:34 filebeat -rw-r--r-- 1 root root 802 Mar 21 14:35 README.md -rw-r--r-- 1 root root 41 Mar 21 14:35 .build_hash.txt drwx------ 9 root root 4096 Mar 30 13:46 .. drwxr-xr-x 5 root root 4096 Mar 30 13:46 .
Mac Download:
curl -L -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-6.7.0-darwin-x86_64.tar.gz tar xzvf filebeat-6.7.0-darwin-x86_64.tar.gz
RPM Download:
curl -L -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-6.7.0-x86_64.rpm sudo rpm -vi filebeat-6.7.0-x86_64.rpm
Step-2) Configure filebeat.yml config file
Checkout filebeat.yml file. It’s filebeat configuration file.
Here is a simple file content.
root@localhost:~/filebeat-6.7.0-linux-x86_64# cat filebeat.yml
###################### Filebeat Configuration Example #########################
# This file is an example configuration file highlighting only the most common
# options. The filebeat.reference.yml file from the same directory contains all the
# supported options with more comments. You can use it as a reference.
#
# You can find the full configuration reference here:
# https://www.elastic.co/guide/en/beats/filebeat/index.html
# For more available modules and options, please see the filebeat.reference.yml sample
# configuration file.
#=========================== Filebeat inputs =============================
filebeat.inputs:
# Each - is an input. Most options can be set at the input level, so
# you can use different inputs for various configurations.
# Below are the input specific configurations.
- type: log
# Change to true to enable this input configuration.
enabled: false
# Paths that should be crawled and fetched. Glob based paths.
paths:
- /var/log/*.log
#- c:\programdata\elasticsearch\logs\*
# Exclude lines. A list of regular expressions to match. It drops the lines that are
# matching any regular expression from the list.
#exclude_lines: ['^DBG']
# Include lines. A list of regular expressions to match. It exports the lines that are
# matching any regular expression from the list.
#include_lines: ['^ERR', '^WARN']
# Exclude files. A list of regular expressions to match. Filebeat drops the files that
# are matching any regular expression from the list. By default, no files are dropped.
#exclude_files: ['.gz$']
# Optional additional fields. These fields can be freely picked
# to add additional information to the crawled log files for filtering
#fields:
# level: debug
# review: 1
### Multiline options
# Multiline can be used for log messages spanning multiple lines. This is common
# for Java Stack Traces or C-Line Continuation
# The regexp Pattern that has to be matched. The example pattern matches all lines starting with [
#multiline.pattern: ^\[
# Defines if the pattern set under pattern should be negated or not. Default is false.
#multiline.negate: false
# Match can be set to "after" or "before". It is used to define if lines should be append to a pattern
# that was (not) matched before or after or as long as a pattern is not matched based on negate.
# Note: After is the equivalent to previous and before is the equivalent to to next in Logstash
#multiline.match: after
#============================= Filebeat modules ===============================
filebeat.config.modules:
# Glob pattern for configuration loading
path: ${path.config}/modules.d/*.yml
# Set to true to enable config reloading
reload.enabled: false
# Period on which files under path should be checked for changes
#reload.period: 10s
#==================== Elasticsearch template setting ==========================
setup.template.settings:
index.number_of_shards: 3
#index.codec: best_compression
#_source.enabled: false
#================================ General =====================================
# The name of the shipper that publishes the network data. It can be used to group
# all the transactions sent by a single shipper in the web interface.
#name:
# The tags of the shipper are included in their own field with each
# transaction published.
#tags: ["service-X", "web-tier"]
# Optional fields that you can specify to add additional information to the
# output.
#fields:
# env: staging
#============================== Dashboards =====================================
# These settings control loading the sample dashboards to the Kibana index. Loading
# the dashboards is disabled by default and can be enabled either by setting the
# options here, or by using the `-setup` CLI flag or the `setup` command.
#setup.dashboards.enabled: false
# The URL from where to download the dashboards archive. By default this URL
# has a value which is computed based on the Beat name and version. For released
# versions, this URL points to the dashboard archive on the artifacts.elastic.co
# website.
#setup.dashboards.url:
#============================== Kibana =====================================
# Starting with Beats version 6.0.0, the dashboards are loaded via the Kibana API.
# This requires a Kibana endpoint configuration.
setup.kibana:
# Kibana Host
# Scheme and port can be left out and will be set to the default (http and 5601)
# In case you specify and additional path, the scheme is required: http://localhost:5601/path
# IPv6 addresses should always be defined as: https://[2001:db8::1]:5601
#host: "localhost:5601"
# Kibana Space ID
# ID of the Kibana Space into which the dashboards should be loaded. By default,
# the Default Space will be used.
#space.id:
#============================= Elastic Cloud ==================================
# These settings simplify using filebeat with the Elastic Cloud (https://cloud.elastic.co/).
# The cloud.id setting overwrites the `output.elasticsearch.hosts` and
# `setup.kibana.host` options.
# You can find the `cloud.id` in the Elastic Cloud web UI.
#cloud.id:
# The cloud.auth setting overwrites the `output.elasticsearch.username` and
# `output.elasticsearch.password` settings. The format is `<user>:<pass>`.
#cloud.auth:
#================================ Outputs =====================================
# Configure what output to use when sending the data collected by the beat.
#-------------------------- Elasticsearch output ------------------------------
output.elasticsearch:
# Array of hosts to connect to.
hosts: ["localhost:9200"]
# Enabled ilm (beta) to use index lifecycle management instead daily indices.
#ilm.enabled: false
# Optional protocol and basic auth credentials.
#protocol: "https"
#username: "elastic"
#password: "changeme"
#----------------------------- Logstash output --------------------------------
#output.logstash:
# The Logstash hosts
#hosts: ["localhost:5044"]
# Optional SSL. By default is off.
# List of root certificates for HTTPS server verifications
#ssl.certificate_authorities: ["/etc/pki/root/ca.pem"]
# Certificate for SSL client authentication
#ssl.certificate: "/etc/pki/client/cert.pem"
# Client Certificate Key
#ssl.key: "/etc/pki/client/cert.key"
#================================ Processors =====================================
# Configure processors to enhance or manipulate events generated by the beat.
processors:
- add_host_metadata: ~
- add_cloud_metadata: ~
#================================ Logging =====================================
# Sets log level. The default log level is info.
# Available log levels are: error, warning, info, debug
#logging.level: debug
# At debug level, you can selectively enable logging only for some components.
# To enable all selectors use ["*"]. Examples of other selectors are "beat",
# "publish", "service".
#logging.selectors: ["*"]
#============================== Xpack Monitoring ===============================
# filebeat can export internal metrics to a central Elasticsearch monitoring
# cluster. This requires xpack monitoring to be enabled in Elasticsearch. The
# reporting is disabled by default.
# Set to true to enable the monitoring reporter.
#xpack.monitoring.enabled: false
# Uncomment to send the metrics to Elasticsearch. Most settings from the
# Elasticsearch output are accepted here as well. Any setting that is not set is
# automatically inherited from the Elasticsearch output configuration, so if you
# have the Elasticsearch output configured, you can simply uncomment the
# following line.
#xpack.monitoring.elasticsearch:
Open filebeat.yml file and setup your log file location:
Step-3) Send log to ElasticSearch
Make sure you have started ElasticSearch locally before running Filebeat. I’ll publish an article later today on how to install and run ElasticSearch locally with simple steps.
Here is a filebeat.yml file configuration for ElasticSearch.
ElasticSearch runs on port 9200.
output.elasticsearch: # Array of hosts to connect to. hosts: ["localhost:9200"]
And you are all set.
Step-4) Run Filebeat
bash-3.2$ sudo chown root filebeat.yml bash-3.2$ sudo ./filebeat -e
Execute above two commands from filebeat root directory and you should see filebeat startup logs as below.
root@localhost:/user/crunchify/filebeat-6.6.2-linux-x86_64# sudo chown root filebeat.yml
root@localhost:/user/crunchify/filebeat-6.6.2-linux-x86_64# sudo ./filebeat -e
2019-03-30T14:52:02.608Z INFO instance/beat.go:616 Home path: [/user/crunchify/filebeat-6.6.2-linux-x86_64] Config path: [/user/crunchify/filebeat-6.6.2-linux-x86_64] Data path: [/user/crunchify/filebeat-6.6.2-linux-x86_64/data] Logs path: [/user/crunchify/filebeat-6.6.2-linux-x86_64/logs]
2019-03-30T14:52:02.608Z INFO instance/beat.go:623 Beat UUID: da7e202d-d480-42df-907a-1073b19c8e2d
2019-03-30T14:52:02.609Z INFO [seccomp] seccomp/seccomp.go:116 Syscall filter successfully installed
2019-03-30T14:52:02.609Z INFO [beat] instance/beat.go:936 Beat info {"system_info": {"beat": {"path": {"config": "/user/crunchify/filebeat-6.6.2-linux-x86_64", "data": "/user/crunchify/filebeat-6.6.2-linux-x86_64/data", "home": "/user/crunchify/filebeat-6.6.2-linux-x86_64", "logs": "/user/crunchify/filebeat-6.6.2-linux-x86_64/logs"}, "type": "filebeat", "uuid": "da7e202d-d480-42df-907a-1073b19c8e2d"}}}
2019-03-30T14:52:02.609Z INFO [beat] instance/beat.go:945 Build info {"system_info": {"build": {"commit": "1eea934ce81be553337f2828bd12131896fea8e4", "libbeat": "6.6.2", "time": "2019-03-06T14:17:59.000Z", "version": "6.6.2"}}}
2019-03-30T14:52:02.609Z INFO [beat] instance/beat.go:948 Go runtime info {"system_info": {"go": {"os":"linux","arch":"amd64","max_procs":2,"version":"go1.10.8"}}}
2019-03-30T14:52:02.611Z INFO [beat] instance/beat.go:952 Host info {"system_info": {"host": {"architecture":"x86_64","boot_time":"2019-01-15T18:44:58Z","containerized":false,"name":"localhost","ip":["127.0.0.1/8","::1/128","50.116.13.161/24","192.168.177.126/17","2600:3c01::f03c:91ff:fe17:4534/64","fe80::f03c:91ff:fe17:4534/64"],"kernel_version":"4.18.0-13-generic","mac":["f2:3c:91:17:45:34"],"os":{"family":"debian","platform":"ubuntu","name":"Ubuntu","version":"18.10 (Cosmic Cuttlefish)","major":18,"minor":10,"patch":0,"codename":"cosmic"},"timezone":"UTC","timezone_offset_sec":0,"id":"1182104d1089460dbcc0c94ff1954c8c"}}}
2019-03-30T14:52:02.611Z INFO [beat] instance/beat.go:981 Process info {"system_info": {"process": {"capabilities": {"inheritable":null,"permitted":["chown","dac_override","dac_read_search","fowner","fsetid","kill","setgid","setuid","setpcap","linux_immutable","net_bind_service","net_broadcast","net_admin","net_raw","ipc_lock","ipc_owner","sys_module","sys_rawio","sys_chroot","sys_ptrace","sys_pacct","sys_admin","sys_boot","sys_nice","sys_resource","sys_time","sys_tty_config","mknod","lease","audit_write","audit_control","setfcap","mac_override","mac_admin","syslog","wake_alarm","block_suspend","audit_read"],"effective":["chown","dac_override","dac_read_search","fowner","fsetid","kill","setgid","setuid","setpcap","linux_immutable","net_bind_service","net_broadcast","net_admin","net_raw","ipc_lock","ipc_owner","sys_module","sys_rawio","sys_chroot","sys_ptrace","sys_pacct","sys_admin","sys_boot","sys_nice","sys_resource","sys_time","sys_tty_config","mknod","lease","audit_write","audit_control","setfcap","mac_override","mac_admin","syslog","wake_alarm","block_suspend","audit_read"],"bounding":["chown","dac_override","dac_read_search","fowner","fsetid","kill","setgid","setuid","setpcap","linux_immutable","net_bind_service","net_broadcast","net_admin","net_raw","ipc_lock","ipc_owner","sys_module","sys_rawio","sys_chroot","sys_ptrace","sys_pacct","sys_admin","sys_boot","sys_nice","sys_resource","sys_time","sys_tty_config","mknod","lease","audit_write","audit_control","setfcap","mac_override","mac_admin","syslog","wake_alarm","block_suspend","audit_read"],"ambient":null}, "cwd": "/user/crunchify/filebeat-6.6.2-linux-x86_64", "exe": "/user/crunchify/filebeat-6.6.2-linux-x86_64/filebeat", "name": "filebeat", "pid": 20394, "ppid": 20393, "seccomp": {"mode":"filter","no_new_privs":true}, "start_time": "2019-03-30T14:52:01.740Z"}}}
2019-03-30T14:52:02.611Z INFO instance/beat.go:281 Setup Beat: filebeat; Version: 6.6.2
2019-03-30T14:52:05.613Z INFO add_cloud_metadata/add_cloud_metadata.go:319 add_cloud_metadata: hosting provider type not detected.
2019-03-30T14:52:05.614Z INFO elasticsearch/client.go:165 Elasticsearch url: http://localhost:9200
2019-03-30T14:52:05.615Z INFO [publisher] pipeline/module.go:110 Beat name: localhost
2019-03-30T14:52:05.615Z INFO instance/beat.go:403 filebeat start running.
2019-03-30T14:52:05.615Z INFO registrar/registrar.go:134 Loading registrar data from /user/crunchify/filebeat-6.6.2-linux-x86_64/data/registry
2019-03-30T14:52:05.615Z INFO [monitoring] log/log.go:117 Starting metrics logging every 30s
2019-03-30T14:52:05.616Z INFO registrar/registrar.go:141 States Loaded from registrar: 0
2019-03-30T14:52:05.616Z INFO crawler/crawler.go:72 Loading Inputs: 1
2019-03-30T14:52:05.616Z INFO log/input.go:138 Configured paths: [/crunchify/tutorials/log/crunchify-filebeat-test.log]
2019-03-30T14:52:05.616Z INFO input/input.go:114 Starting input of type: log; ID: 7740765267175828127
2019-03-30T14:52:05.617Z INFO crawler/crawler.go:106 Loading and starting Inputs completed. Enabled inputs: 1
2019-03-30T14:52:05.617Z INFO cfgfile/reload.go:150 Config reloader started
2019-03-30T14:52:05.617Z INFO cfgfile/reload.go:205 Loading of config files completed.
Step-5) Result
Next step is for your to check who logs are coming to Elastic Search and how you are visualizing. We will go over detailed tutorial on that very soon. Stay tuned.
What’s next? Setup Elastic Search
How to Install and Configure Elasticsearch on your Dev/Production environment?